Cybersecurity Awareness Month 2016: Can you spot a malicious or compromised site?
Malicious and compromised websites are typically fake sites that resemble their legitimate counterparts down to every detail—except for the URL. Users rarely intend to stumble upon such a site but find themselves here by either mistyping a URL or browsing aimlessly. The term used for these nearly legitimate URLs is known as “typosquatting.” Typosquatting sites are dangerous because they may be full of malware that will infect computers and systems.
The following signs will help you distinguish a fake site from the real deal—drastically decreasing your chance of visiting a malicious or compromised site:
- Look for an SSL Certificate (https): Legitimate sites that handle sensitive information will use encryption, which is usually indicated by a padlock and “https” in the URL. Fake sites are not typically secure; if the site does not include “https” in the URL, it is likely a malicious site.
NOTE: Hackers are beginning to set up their own secure phishing sites. A site could have “https” but fail under the other categories; so stay vigilant.
- Recognize strange behavior on a legitimate site: If you are on a legitimate site, but the pages advertise free goods or services via pop-ups instead, this could mean that the site has been compromised. More often than not, the website owner is unaware that the site is no longer safe. When a commonly visited website is compromised, this hacking technique is known as a “watering hole” attack and is often used to infect users’ systems with malware.
- Notice unwanted downloads: A site prompting you to download an application, to install/update Flash Player, or to remove a virus are all signs that something is fishy about a webpage. Before you click on a pop-up to run a (fake) antivirus scan or to remove a virus that a site has identified on your system, consider that this is one of the oldest tricks in the book. Do not install or download from a pop-up because your system will have a greater chance of becoming infected by a form of malware.
- Identify an unusual URL: An imposter website can resemble the actual one to the extent of the look and feel; however, the URL will not match. This is a dead giveaway that the site is a typosquatted site. Take time to inspect URLs for suspicious misspellings, punctuation, or possibly long and garbled text. If you are using a web browser that only displays the domain instead of the full address, click on the address bar to reveal the full URL. Additionally, if you see a suspicious link in an email or on a website, hover over the hypertext to preview the URL before clicking on it.
- Pay attention to security tools warnings: If someone sends you a link to a website that looks strange, do not click on the link. Use tools to check if a website is safe or if it is on blacklists (which are maintained by security organizations) of known malicious sites. Reliable site advisors, such as McAfee’s WebAdvisor, can also help you avoid potentially malicious sites. On that same note, personal software inspectors like Secunia’s Personal Software Inspector will support you in maintaining updates on software installed on your personal computer.
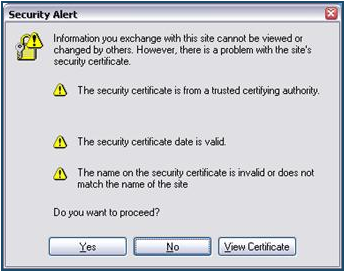
Below is an example of an invalid certificate:
For more information about malicious or compromised websites and how to protect yourself, contact VUIT Security Operations at vuit.security.operations@vanderbilt.edu.