Cybersecurity Awareness Month 2016: The 411 on ransomware
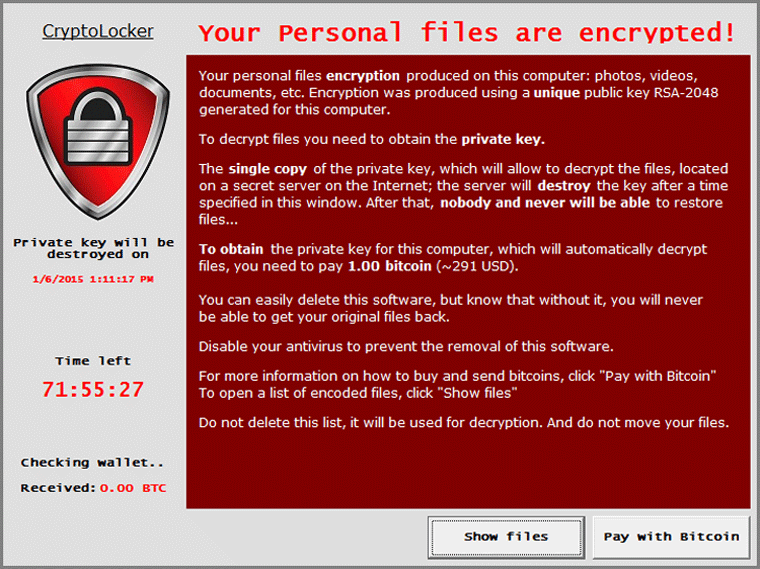
Ransomware is a type of malware that is frequently delivered through phishing emails to an end user. Today, most variants of ransomware are designed to encrypt files on the infected system and network. This type of ransomware is called crypto-ransomware. Other variants have been known to erase files. Once blocking access to the system is completed, the ransomware will pop up a “ransom demand” (as pictured below) requiring that you pay a ransom in order to regain access to your system. This ransom can range from $200 to $800 worth of bitcoin or gift cards per infected system. According to the Multi-State Information Sharing and Analysis Center (MS-ISAC), ransomware incidents have surged in 2016.
How ransomware works
Ransomware is usually delivered through phishing emails containing malicious attachments. These attachments contain file extension types, such as .pdf, .doc, .docx, .xls, .xlsx, and .exe, and flaunt legitimate-like names along the lines of a report, invoice, or spreadsheet. However, instead of the attachment being what it claims to be, it contains malicious code that is activated by opening the attachment.
The other way attackers leverage ransomware is through an exploit kit hosted on a website. After either receiving a phishing email or browsing to a malicious site (using an outdated browser or a browser with an outdated plugin), the user navigates to a website containing malicious code—thus, infecting his/her system and falling victim to ransomware.
Though anti-virus (AV) software certainly helps, it does not guarantee 100 percent protection. Attackers use tools that create a malicious code that can bypass most brands of AV programs. That being said, keeping your AV and its definitions up to date will drastically decrease the chances of malicious code overcoming your AV and infecting your system.
How to protect yourself
Besides the basic prevention measures of patching your main operating system and programs and updating your mobile devices, follow the steps below to protect yourself against phishing and ransomware attacks:
- Use up-to-date anti-virus. Run an up-to-date anti-virus program from a trusted vendor, and select the option for the software to automatically update.
- Use up-to-date anti-malware. Run an up-to-date anti-malware program from a trusted vendor, and select the option for the software to automatically update.
- Use a non-privileged account for day-to-day normal activities. Only use the privileged-type account when absolutely necessary. A privileged-type account is an account that is in the “administrators” group in Windows or in the “root” group in Linux/Unix (GID of 0).
- Keep offline backups of your important data. Offline means that the backed up files are neither immediately available nor connected to the system through USB or network connections. Some ransomware has the ability to encrypt shared file systems or cloud-based file systems that are mounted to the system.
- Don’t click on hyperlinks in emails. Instead, hover your mouse cursor over the hyperlink to check that the underlying URL is actually going to where it claims to be going in the displayed text. When using an embedded link from an email, right-click on the link and select “copy hyperlink,” then paste it into your browser to verify that the pasted URL is the correct address before navigating to the address. For financial websites or an Outlook email web access link, manually type in the URL or select the link from your “favorites” bookmark. Do not use a link contained in an email to navigate to financial sites or email hosting sites.
- Don’t open file attachments from email unless you know the sender and are expecting an attached file. If you are not expecting an attachment from the sender, do not click on or open any attachment. Check with the sender first to verify that he/she did in fact send you the unexpected attachment. In doing so, use a different communication method to contact the sender, such as a phone call, text, or instant message. If email is the only form of contact you have with the sender, email him/her asking for verification through a phone call.
What to do in the event of a ransomware attack
If any Vanderbilt system becomes compromised through a ransomware attack, immediately disconnect the system from the network either by removing the network cable or by turning off the wireless connection. Notify VUIT Incident Response (vuit.incident.response@vanderbilt.edu) immediately in order to contain and resolve the ransomware incident.
Remember: Vanderbilt IT and HR will NEVER ask you to verify an account for ANY reason via email. If you receive an email stating that you need to re-verify your account, please report it to the VUIT Help Desk by calling (615) 343-9999 or submitting a ticket.
How do I report a suspicious email?
In Outlook, when you forward the suspected phishing email, forward it as an attachment. Forwarding the suspicious email as an attachment will preserve email headers, any attached files and other pertinent information. To perform this function in Outlook, select the “home” tab, click on the “respond” section, and select “more” from the dropdown menu. After clicking “more,” select “forward as attachment.”
For additional general information about phishing and how to protect yourself, please contact VUIT Incident Response at vuit.incident.response@vanderbilt.edu.